
Learning Resource
Managing Infrastructure in Amazon Using EC2, CloudWatch, EBS, IAM, and CloudFront
by Aishwarya Anand
Introduction
The Amazon Web Services (AWS) management console provides a visual way to manage all the AWS tasks, such as working with Amazon storage buckets, launching Amazon EC2 instances, or setting Amazon CloudWatch alarms. Each service has its own console accessed from the main console. The AWS management console also provides a way to get to information about accounts and billing.
Amazon EC2 provides computing capabilities in the cloud. It has a very simple service interface through which a user can obtain and configure capacity efficiently, which ensures that the capacity is used in a predictable manner.
EC2 not only maintains the confidentiality of user data that is stored in the cloud but also places the user instances in a virtual private cloud (VPC) with an IP range specified by the customer [2]. The customer can decide on the instances to keep private and the ones to expose to the world. There are security groups that allow a customer to specify and control the inbound and the outbound traffic to and from an instance. The customer pays on an hourly basis. The service provides automatic scaling, which eliminates the burden of handling traffic spikes. Instances are available on-demand and can also be reserved [2].
To use Amazon EC2 [2]:
- Select a preconfigured, templated Amazon Machine Image (AMI) to get running immediately.
- Configure security and network access on an Amazon EC2 instance.
- Choose which instance type(s) you want, and then start, terminate, and monitor as many instances of the AMI as needed.
- You can also attach persistent block storage to your instances.
- Pay only for the resources that you actually consume, such as instance hours or data transfer.
Amazon EC2 provides the following features [5]:
Instances: Virtual computing environments
- AMI: Preconfigured templates for the instances. The templates package the bits needed for a server (including the operating system and additional software)
- Instance types: Various configurations of CPU, memory, storage, and networking capacity for instances
- Key pairs: Secure login information for instances (AWS stores the public key, and you store the private key in a secure place)
- Instance store volumes: Storage volumes for temporary data that's deleted when an instance is stopped or terminated
- EBS volumes: Persistent storage volumes for data using Amazon Elastic Block Store (Amazon EBS)
- Regions and availability zones: Multiple physical locations for resources, such as instances and Amazon EBS volumes
- Security groups: A firewall that enables the specification of the protocols, ports, and source IP ranges that can reach instances
- Elastic IP addresses: Static IP addresses for dynamic cloud computing
- Tags: Metadata that can be created and assigned to Amazon EC2 resources
- Virtual private clouds (VPCs): Virtual networks to create, which are logically isolated from the rest of the AWS cloud, and can be optionally connected to a network
AWS CloudWatch
AWS CloudWatch, a service provided by Amazon, collects measurements of AWS resources so they can be easily accessed or you can receive timely notifications. It reduces the time to detect and recover from issues.
AWS CloudWatch allows the monitoring of AWS resources in real time without installing additional software. AWS resources that can be monitored in CloudWatch are [11]:
- EC2 instance
- EBS volume
- Autoscaling groups
- Elastic Load Balancer
CloudWatch lowers the operational overhead and works well with AWS. No configuration is necessary, and alarms can be set for different situations
Users get many things for free, such as CPU and input/output (I/O) stats.
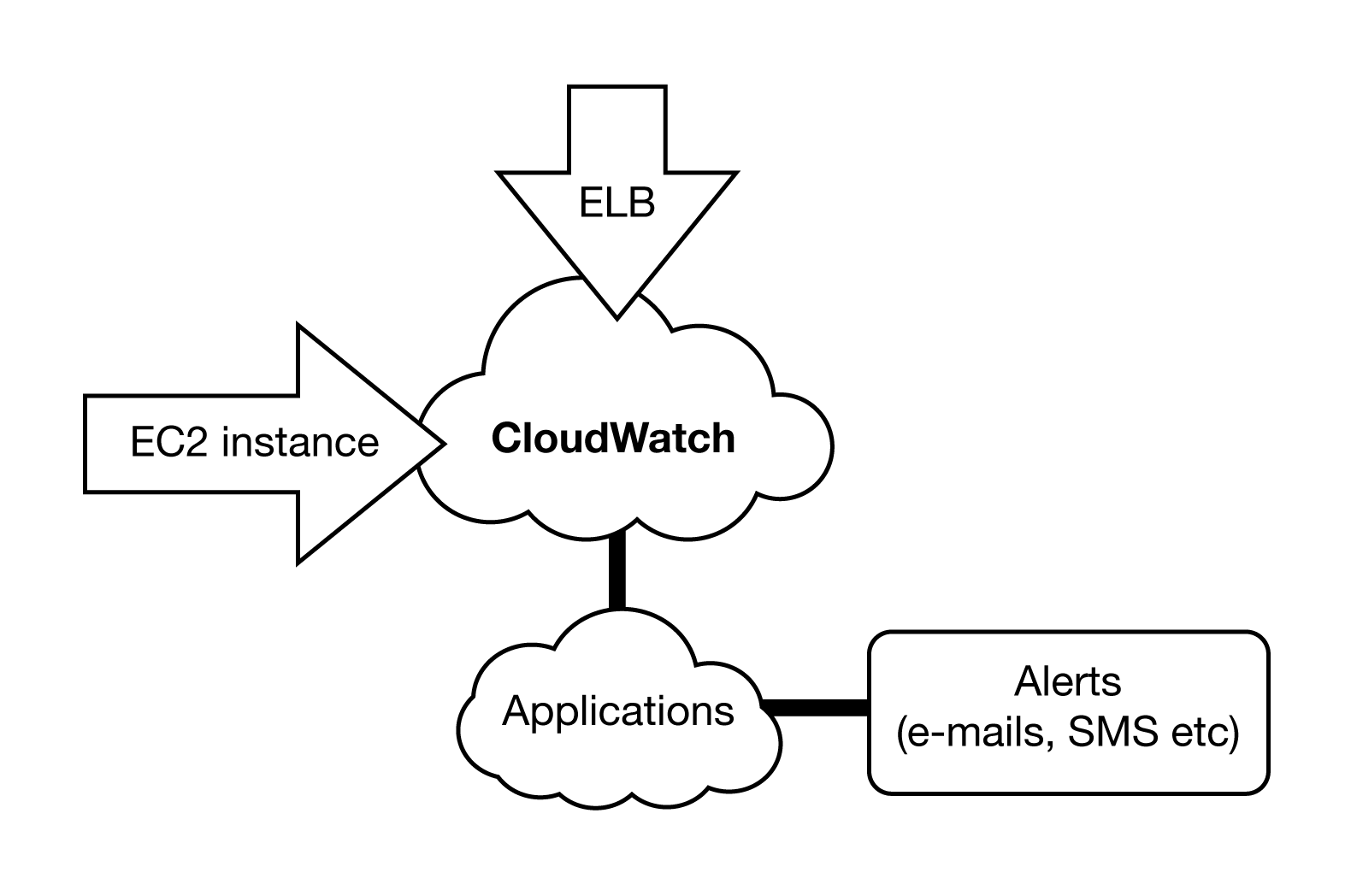
Basic CloudWatch Architecture
For example, you can use CloudWatch to monitor the CPU and disk reads of EC2 instances and then use this data to determine whether additional instances should be launched to handle that load [12].
Alarms
An alarm watches a single metric over a specified time period and performs one or more actions based on the value of the metric relative to a given threshold over a number of time periods. The action is a notification sent to an Amazon Simple Notification Service or Auto Scaling policy.
The following steps are followed:
- Choose a metric in CloudWatch
- Set a threshold value
- Assign an action to take when the threshold breaches; for example, e-mail or simple messaging service (SMS).
EBS (Amazon Elastic Block Store)
Amazon Elastic Block Store (EBS) is essentially a virtual hard drive—a storage volume that can be attached to an EC2 instance. It includes [6]:
- raw storage
- has limits from 1GB to 1000GB
- attached to EC2 instance in an availability zone
- billed on storage space and I/O operations (per Gb)
EBS allows for storage volumes from 1 GB to 1 TB. File systems can be created on top of Amazon EBS volumes or used in any other way (such as a hard disk). Amazon EBS volumes are network-attached, and persist independently from the life of an instance. The volumes can be attached to any running instance in the same availability zone. EBS can be leveraged as an Amazon EC2 instance's boot partition or attached to a running Amazon EC2 instance as a standard block device. EBS volumes that are attached to an Amazon EC2 instance are exposed as storage volumes that persist independently from the life of the instance.
Amazon EBS volumes offer improved durability over local Amazon EC2 instance stores, as Amazon EBS volumes are automatically replicated on the back end (in a single availability zone). It has an annual failure rate of 0.1 percent to 0.4 percent, which is much less than normal hard drives.
Amazon EBS provides the ability to create point-in-time consistent snapshots of volumes that are then stored in Amazon S3, and automatically replicated across multiple availability zones. These snapshots can be used as the starting point for new Amazon EBS volumes, and can protect data for long-term durability. These snapshots can be shared with coworkers and other AWS developers.
Amazon EBS provides two volume types: standard volumes and provisioned IOPS volumes. Standard volumes are designed for applications with moderate I/O requirements. They are also suited for use as boot volumes or applications where I/O can be bursty. Provisioned IOPS volumes offer storage with consistent and low-latency performance, and are designed for applications with I/O-intensive workloads such as databases [2].
Amazon EBS Volumes
An Amazon EBS volume is a durable, block-level storage device that can be attached to a single EC2 instance. Amazon EBS volumes can be used as primary storage for data that requires frequent updates, such as the system drive for an instance or storage for a database application. Amazon EBS volumes persist independently from the running life of an EC2 instance. After a volume is attached to an instance, it can be used like any other physical hard drive [7].
Amazon EBS Snapshots
The process of moving an EBS volume to Amazon S3 is by taking a snapshot, which is used for backup and cloning. An Amazon EBS snapshot is a backup copy of an Amazon EBS volume that is stored in Amazon S3. Snapshots are incremental backups, which means that only the blocks on the device that have changed after the most recent snapshot are saved. When a snapshot is deleted, only the data exclusive to that snapshot is removed. Active snapshots contain all of the information needed to restore data (from the time the snapshot was taken) to a new Amazon EBS volume [7].
Auto Scaling
AWS Auto Scaling grows and shrinks the number of instances attached to an application in case of an event. It allows a user to automatically scale Amazon EC2 capacity up or down according to requirements. With Auto Scaling, the Amazon EC2 instances scale up seamlessly during demand spikes to maintain performance, and scale down automatically when the demand is low to minimize costs. Auto Scaling is particularly suited for applications that experience variability in usage [8] .
Auto Scaling can:
- manage Amazon EC2 capacity automatically
- maintain the right number of instances for the application
- operate a healthy group of instances
- scale instances according to needs
Auto Scaling frees the user from having to predict huge traffic spikes accurately and plan for provisioning resources. It allows a user to build a fully scalable and affordable infrastructure on the cloud. Consider a common web application scenario in which you run multiple copies of an application simultaneously to serve the incoming customer traffic. These multiple copies of your application are hosted on identical Amazon EC2 instances, each of which is handling customer requests. Auto Scaling manages the launch and termination of these EC2 instances [10].
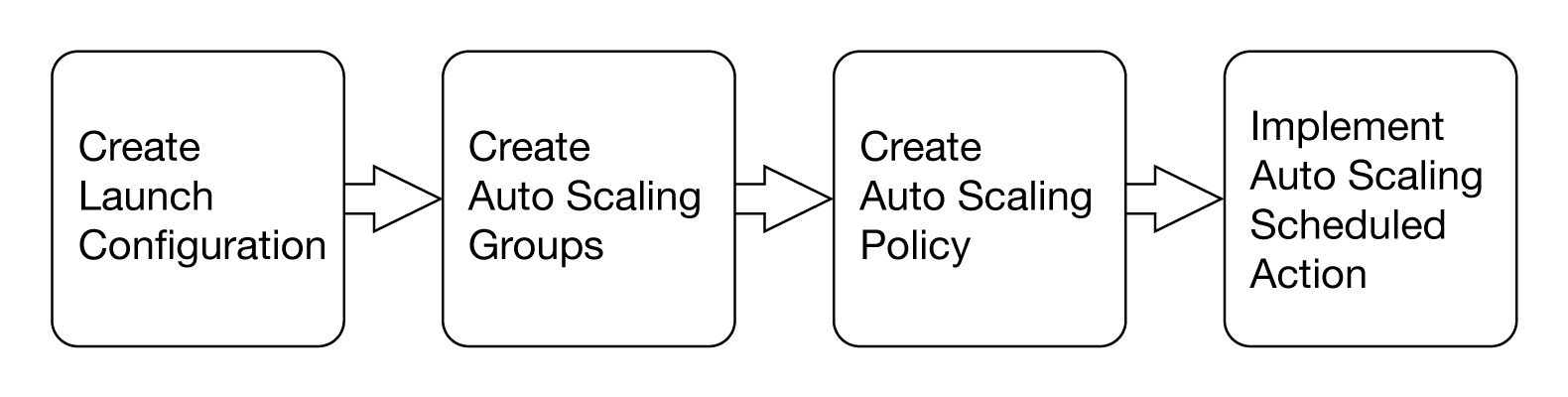
Implementing AWS Auto Scaling [8]
Under Auto Scaling, EC2 instances are categorized into groups. A user creates groups by defining the minimum, maximum, and, optionally, the desired number of running EC2 instances the group must have at any point for the purposes of instance scaling and management.
An Auto Scaling group uses a launch configuration to launch EC2 instances. The user creates the launch configuration by providing information about the image to use to launch EC2 instances, such as the size of the image or the instance type. In addition to creating a launch configuration and an Auto Scaling group, the user also creates a scaling plan for the group. A scaling plan tells Auto Scaling when and how to scale. A scaling plan can be created based on the occurrence of specified conditions (dynamic scaling), or it can be created based on a specific schedule.
IAM (Identity and Access Management)
AWS is mainly targeted at organizations that have multiple users or various systems that use AWS products such as EC2 and Amazon S3. IAM is used to manage all the users of AWS by having a central control, providing access keys, and granting user permissions that control the access to AWS resources.
The basic entities in IAM are users and groups. Permissions are granted to these entities that enable them to access AWS resources. IAM manages users and their permissions by using IAM to query the application programming interface (API), with which the customer can make direct calls to the IAM web service. Whenever a request is sent to AWS, it must include authentication information so that AWS can verify the authenticity of the user request. AWS uses this information to recreate the customer signature, which it compares with the one that is sent. If they match, the user is allowed to access AWS.
IAM supports GET and POST requests for all actions. GET requests are browser-dependent and have a limitation of URL (Uniform Resource Locator) size, whereas POST does not have any such limitation and is used for URLs of larger size. IAM users can sign their requests with an access key ID and a secret key, or use the AWS security token service that generates temporary security credentials. These security credentials not only authenticate a user but also determine whether there is permission to access those resources [13].
IAM not only manages all the users and their permissions centrally but also provides security credentials like access keys and user permissions to authenticate users. Without IAM, companies would have multiple AWS accounts and would have to manage them separately. Every account would have different billing, and there would be no controls over the tasks of a particular user.
IAM also allows central control over data, and thus no data is lost when an employee leaves the organization. IAM also allows control over the network by which the employees can access AWS resources only from the organization's corporate network using SSL (Secure Sockets Layer). You receive a single consolidated bill for multiple AWS accounts. An organization can have multiple AWS accounts. One account becomes the paying account that pays for its own charges and the charges of the linked AWS accounts.
IAM includes the following:
- Users: Create individual users
- Groups: Manage permissions with groups
- Permissions: Grant least privilege
- Password: Configure a strong password policy
- MFA: Enable MFA for privileged users
- Roles: Use IAM roles for EC2 instances
- Sharing: Use IAM roles to share access
- Rotate: Rotate security credentials regularly
- Conditions: Restrict privileged access further with conditions
- Root: Reduce/remove use of root
IAM creates multiple users and assigns them different permissions. It also grants temporary access to some users by assigning them temporary security credentials. IAM also provides federated user access to those who do not have an AWS account.
IAM Group
IAM Group is a service that provides a collection of IAM users. It allows you to specify a set of permissions for different users in the group. An IAM user can belong to multiple groups, and permissions can be assigned to new users by adding them to appropriate groups. When a user is moved to another department in the organization, that user can be removed from the old group and added to the new group.
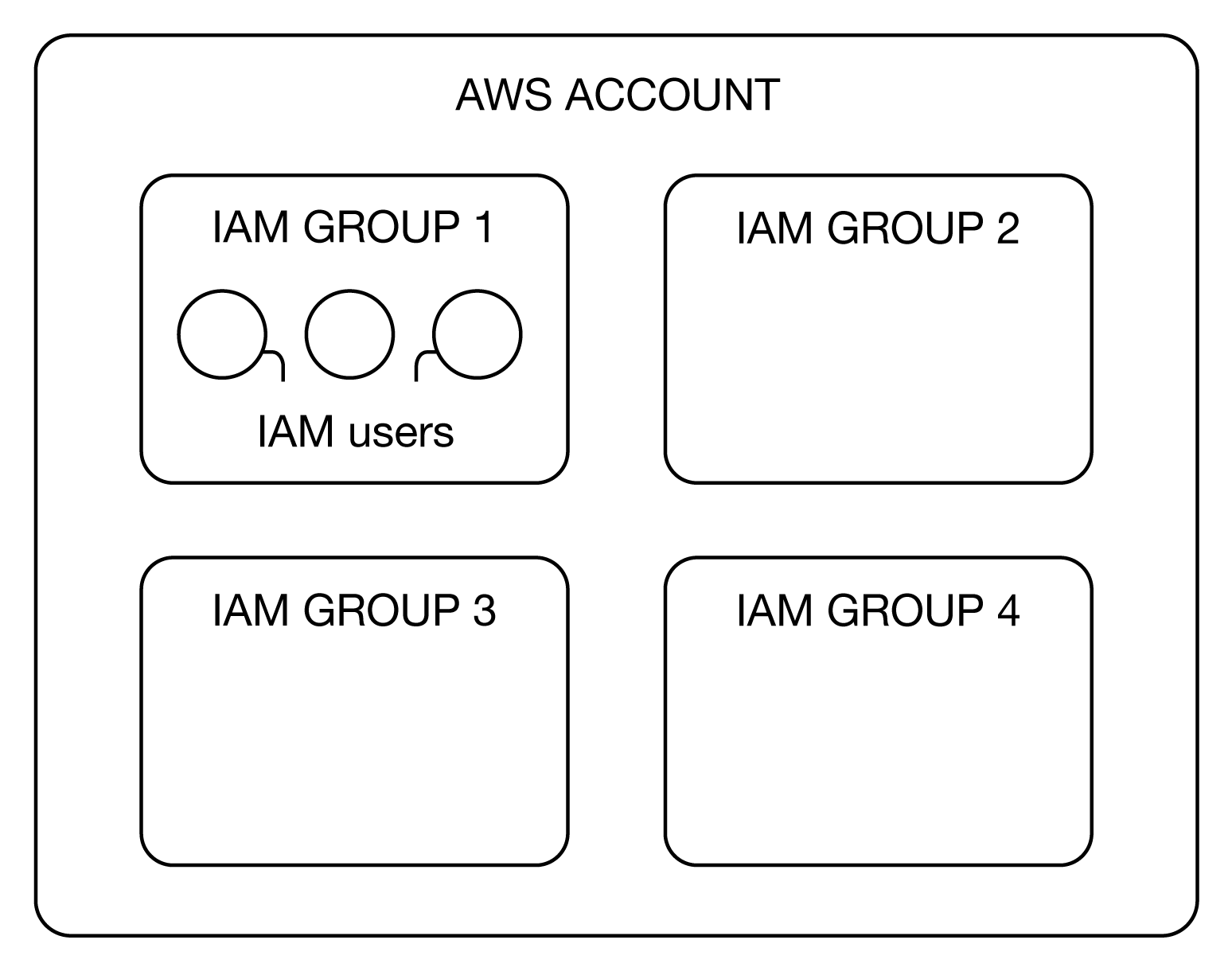
IAM Groups and Users
IAM Users
IAM Users is the entity that is created to interact with AWS. IAM users provide identity to employees of an organization with which they can sign into their AWS management console and access the services they have permission to access. An IAM user is not always a person; it is an identity associated with some permissions. IAM users are provided with a username and password that uniquely identifies the user to AWS.
IAM username and password: An organization has a large number of users that access the AWS account. AWS IAM allows the creation of multiple unique user identities for all the users accessing the account. This enables all the users in an organization to access the account with unique IDs and passwords. It also stratifies users by granting them different permissions—some users get administrative-level permissions whereas some get read-only permissions.
The security of a user's credentials can be enhanced by enabling multifactor authentication for the IAM users.
Multifactor authentication: AWS allows only authenticated users to access the AWS account with the help of a username and password. To provide an extra layer of security, an authentication code is generated from a MFA (multifactor authentication) device. This additional code needs to be entered by the user along with the username and password to sign into the AWS website. It can be used for both the root account as well as the IAM account.
IAM Roles
A role allows a set of permissions to be defined to access the resources that a user or service needs, but these permissions are not attached to an IAM user or group. Instead, many applications and AWS services such as Amazon EC2 can assume roles during runtime. When a role is assumed, AWS returns temporary security credentials that the user or application can use to make a programmatic request to AWS. It temporarily delegates access to users or services that do not have access to AWS resources. For example, a user in an AWS account might need access to resources in another account.
When you create a role, you specify two policies:
- Trust policy: It specifies who is allowed to assume the role, i.e., the principal.
- Access policy: It defines what resources the principal is allowed to access.
IAM Permissions
There are a number of permissions granted to the customer that provide access to one or more resources. These permissions are basically of two types: user-based and resource-based.
- User-based permissions specify the permissions associated with a specific user.
- Resource-based permissions determine the entities that have access to particular resources.
IAM Policies
To assign permission to a user, group, or resource, a policy is created. A policy is a document that explicitly lists permissions. It allows the following to be specified:
- Action: The actions the user will be allowed.
- Resources: The resources on which the action will be allowed.
- Effect: The effect when a user requests access—allow or deny.
IAM Policies control access regardless of the interface. For example, you could provide a user with a password to access the AWS Management Console, and the policies for that user would control what the user can do in the console.
CloudFront
Amazon CloudFront is a content delivery network that delivers web content with the lowest latency. It quickly distributes static as well as dynamic web content such as image files and HTML pages. CloudFront delivers the content through the various edge locations that Amazon has around the world [14].
There is a time period defined for which the content stays in the edge location. After the object has been in the edge location for the specified time, CloudFront retrieves it from an Amazon S3 bucket or a web server, which is the source of that content when the next request for the object is made. It checks whether the version in the edge location is the latest. If so, CloudFront delivers it to the user. If the version is not the latest, then the source sends the latest version to CloudFront, and CloudFront delivers the object to the user.
In the figure below, a user accesses a website—it places requests for one or more objects. The request is then routed to the CloudFront edge location that can serve the user's request. If the CloudFront cache contains the latest version of the object that the user has requested, it returns it to the user. If the latest version is not present in the edge location, the edge location extracts the files from the source, which can be an Amazon S3 bucket or a web server located at Amazon's data center. This object is then sent to the user.
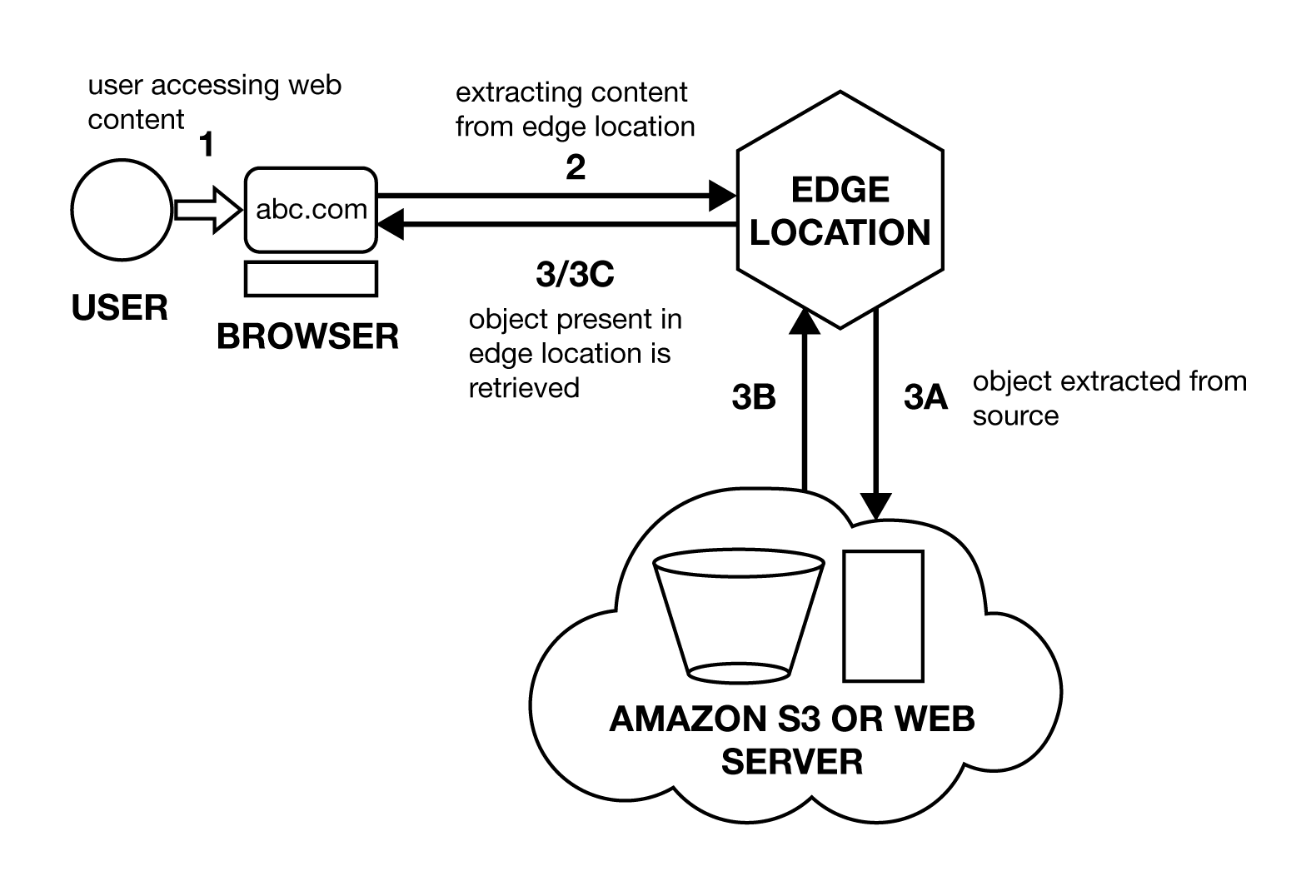
Delivering Content Using CloudFront
You create a CloudFront distribution that tells CloudFront which origin servers to get files from when users request the files through a website or application. It basically contains all the configuration settings such as Amazon S3 bucket information, access control information, whether HTTPS is required to access the content, whether access logs are to be created, etc.
Distributions are of two types:
Web distributions: Web distributions are used to serve web content such as HTML pages, image files and more over HTTP or HTTPS, on-demand multimedia content, or a live event like a concert in real time.
RTMP distributions: RTMP distributions use the Amazon S3 bucket as origin and streams media files using Adobe Media Server and Adobe Real-Time Messaging Protocol (RTMP)
An original server stores files such as web pages and images. These are known as objects. Objects in the Amazon S3 bucket can be made visible to the public so that anyone who is aware of the CloudFront URLs for the object can access them. The objects can also be kept private with access controlled.
CloudFront provides optional log files which inform about the user requests that have been made. Whenever an end user makes a request for an application, a request is routed by CloudFront to the appropriate edge location. CloudFront writes data about each request to a log file. CloudFront periodically puts this log file in an Amazon S3 bucket that you specify.
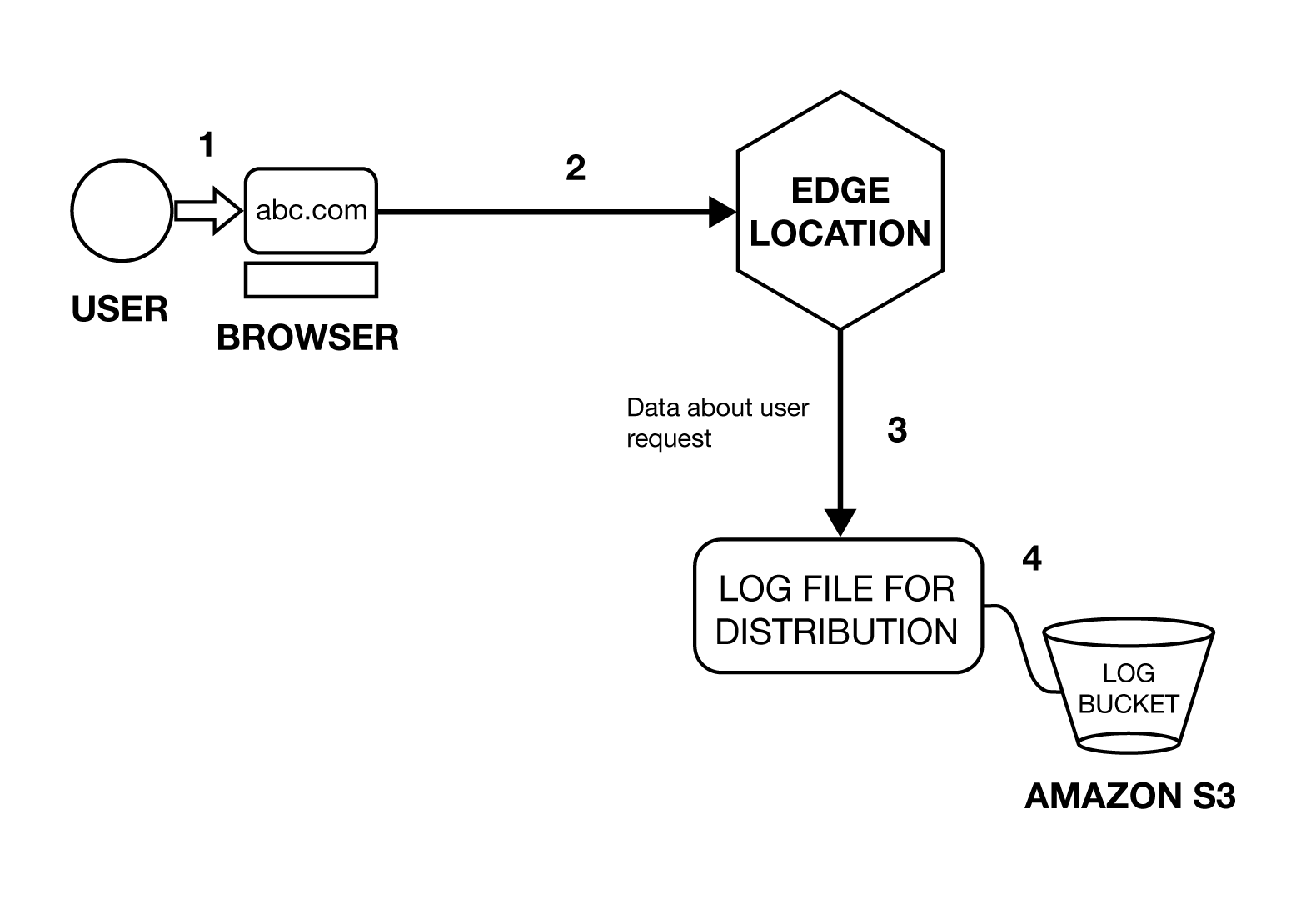
Access Logs In CloudFront
There are a number of organizations that distribute their content via the Internet and want to restrict access to various documents and media files. They can serve their private content securely using CloudFront. For example, users can use special signed URLs to access private content. Access to objects can be restricted in CloudFront edge caches as well as in Amazon S3 buckets. Signed URLs for objects can be created by specifying an ending date and time, after which the URL is not valid. A part of the signed URL is hashed and signed using a private key from the key pair.
The content in the Amazon S3 bucket can be secured by using CloudFront URLs for access as shown in the figure below. This prevents any user from bypassing CloudFront and using an Amazon S3 URL to access the content.
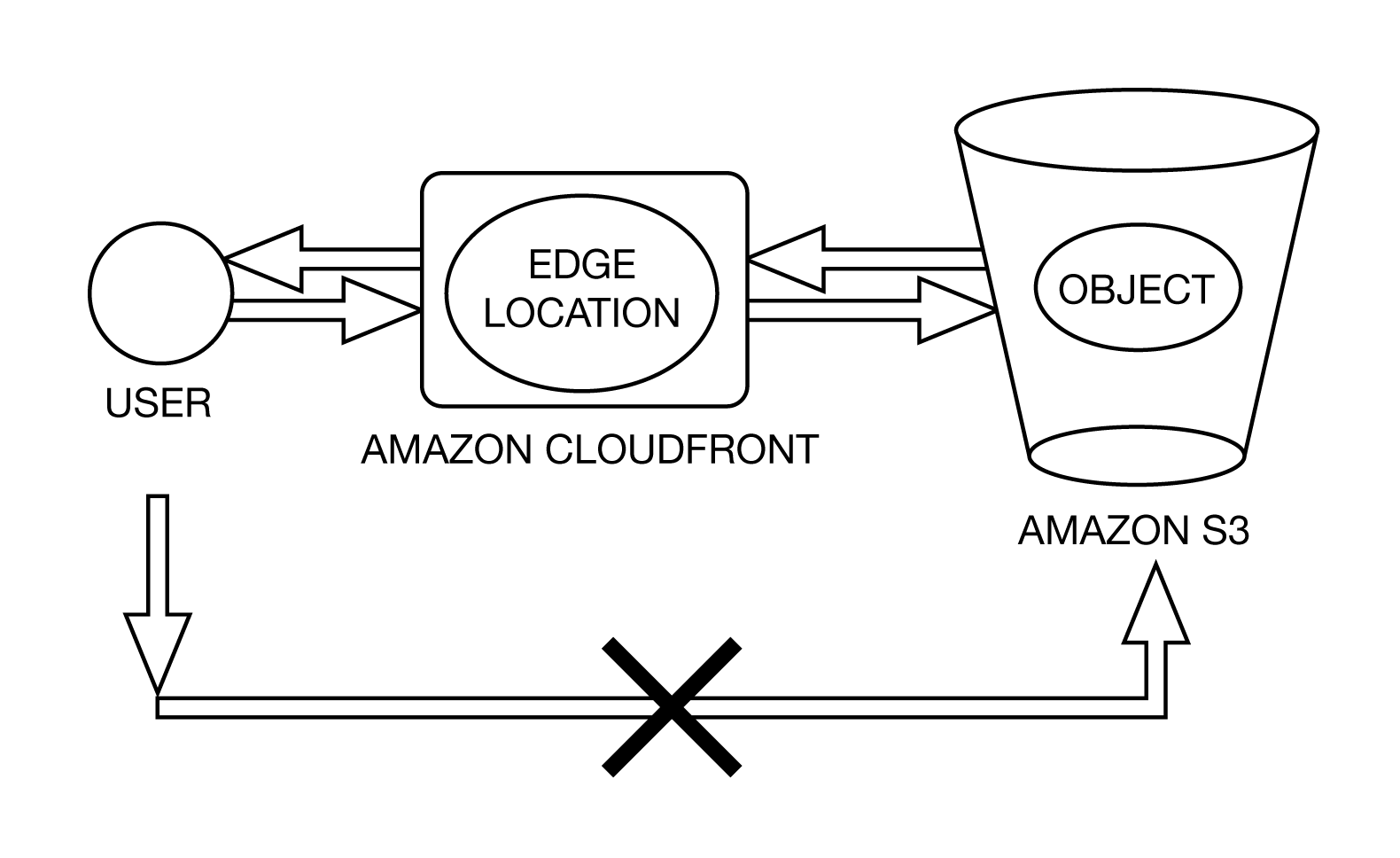
Secured Access Using CloudFront [14]
Conclusion
There are a number of cloud providers in the market today. Our focus is on Amazon, which has guaranteed security through its Amazon elastic compute cloud (EC2) architecture. The beauty of EC2 is that it provides capabilities such as load balancing and automatic scaling.
Amazon maintains the confidentiality of the data by IAM, multifactor authentication, and access keys; it also maintains the integrity of the data by HMAC (Hash-Based Message Authentication Code) and S3 server side encryption. Amazon is also known for its EC2's availability i.e. 99.95%. Amazon's IAM manages users and their access permissions. It centrally controls the users, their security credentials, and their resources.
References
[1] Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J., & Brandic, I. (2009). Cloud computing and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th utility. Future Generation Computer Systems, 25(6), 599–616.
[2] Anand, A. (2015). Infrastructure management in Amazon-EC2 instance. International Journal of Applied Engineering and Research, 10(35).
[3] Amazon Web Services. (n.d.). Auto scaling. Retrieved from http://aws.amazon.com/autoscaling/
[4] AWS management console (n.d.). Getting started guide (version 1.0). Retrieved from http://docs.aws.amazon.com/awsconsolehelpdocs/latest/gsg/getting-started.html
[5] Amazon Web Services. (n.d.). AWS elastic compute cloud user guide (API version 2014-02-01). Retrieved from http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/concepts.html
[6] CBT Nuggets. (n.d.). 07-AWS storage—Elastic Block Storage (EBS).
[7] Amazon Web Services. (n.d.). Amazon elastic compute cloud, user guide (API version 2014-02-01), Amazon Elastic Block Storage. Retrieved from http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/AmazonEBS.html
[8] CBT Nuggets.(n.d.). 06-AWS elasticity—components of auto scaling.
[9] Amazon Web Services. (n.d.). AWS elastic compute cloud user guide (API version 2014-02-01), Amazon Elastic Block Storage. Retrieved from http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/AmazonEBS.html
[10] Amazon Web Services. (n.d.). Auto scaling docs, developer guide. Retrieved from http://docs.aws.amazon.com/AutoScaling/latest/DeveloperGuide/WhatIsAutoScaling.html
[11] Amazon Web Services. (n.d.). AWS re: invent RMG 203 cloud infrastructure and application [video].
[12] Amazon Web Services. (n.d.). Amazon CloudWatch, developer guide (API Version 2010-08-01).
[13] Amazon Web Services. (n.d.). http://docs.aws.amazon.com/AmazonCloudWatch/latest/
[14] Amazon Web Services. (n.d.). Amazon CloudWatch, developer guide (API Version 2010-08-01).
[15] Amazon Web Services. (n.d.). AWS Identity and Access Management, using IAM, API Version 2010-05-08. Retrieved from http://awsdocs.s3.amazonaws.com/IAM/latest/iam-ug.pdf
[16] Amazon Web Services. (n.d.). Amazon CloudWatch, developer guide (API Version 2014-01-31). Retrieved from http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/Introduction.html
Licenses and Attributions
Managing Infrastructure in Amazon using EC2, CloudWatch, EBS, IAM and CloudFront by Aishwarya Anand from International Journal of Engineering Research and Technology is available under a Creative Commons Attribution 4.0 International license. UMGC has modified this work and it is available under the original license.